How to Setup and Install FirewallD on CentOS 7
Many Linux distributions have a firewalld as their firewall management solution, and it acts as a front-end controller for the iptables. The firewalld or firewall-cmd supports both IPV4 and IPV6 networks. Its daemon manages a different set of rules using entities, and these entities are “zones”. The zones are the set of rules that directs what traffic should be allowed in a network depending on the trust. The rules set in firewalld is either permanent or immediate. If any rule gets newly added or edited, then the behavior of firewalld also gets modified. But if the newly added or modified rules are not flagged as –permanent, then the old rules get reverted at the next boot. The prerequisite for enabling firewalld on CentOS 7 is a sudo privileged user and command-line access.
Install FirewallD and Enable to Start at Boot
By default, the firewalld is pre-installed in CentOS 7. To check if firewalld is running in the system, you can run the following command.

If you are not able to see any active firewalld installed, you can install firewalld using the following command.

If you want to start the firewalld service at boot, then you need to enable and reboot the service after firewalld installation.

After the reboot, the firewall gets enabled, and your network interfaces get configured into zones. Also, the rules associated with the zones get applied to the associated interfaces.
To check if the service is running and reachable, you can run the following command. You should get the output as running if the firewall is up and running with the default configuration.

If you get the output as masked, then we need to unmask the symlink by using the following command.

Firewall Zones
A firewall establishes ‘zones’, and each network zones has its set of rules. This set of rules orders what traffic should be accepted or declined in a network. This set of rules provides flexibility compared to iptables. By using this approach, you can set different zones for specific networks.
To list all the available zones in the network, you can run the following command.

If you have just installed firewalld, then you should get an output similar to the one shown below.
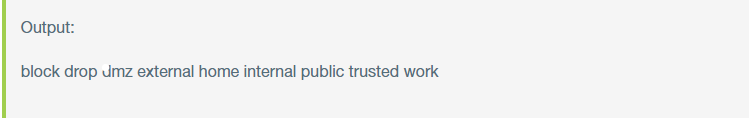
The above output displays the pre-configured zones. If you want to check the default zone, run the following command.

Some of the pre-configured zones and zone descriptions are listed below:
drop:
If you want to set the lowest level of trust, then you can use the drop zone. This zone drops all the incoming connections without reply and only allows the outgoing connection.
block:
This zone is similar to that of the drop zone. But in this zone, all the incoming requests are rejected with an icmp-host-prohibited or icmp6-host-prohibited message
public:
The public zone allows only selected incoming connections on a case-by-case basis. This zone does not trust other PCs and represents the public.
external:
External networks use the firewall as your gateway. We can configure the external zone for NAT masquerading. This zone makes your network private and but reachable.
internal:
This internal zone is just opposite to the external zone, and it gets used for the internal portion of a gateway.
dmz:
This zone is used by PCs that don’t have access to the rest of your network. The dmz zone only allows certain incoming connections.
work:
Work machines use the work zone, and it trusts almost all computers in the network.
home:
A home computer uses the home zone, and this zone trusts most of the other computers.
trusted:
This zone is used casually and trusts all of the machines in the network.
To check the active firewall zone, run the following command.

Firewall Zone Rules
To list all the rules linked with the default zone, you need to run the following command.

To list rules linked with a particular zone, you need to run the following command.
For example,

How to Change Zone of an Interface
By using the below command, you can reassign a zone to a network interface. In this command, the –zone flag is used to specify the zone, and the –change-interface flag is used to specify the network interface.

With this above example, the firewalld should have applied the external zone on all traffic coming through the network interface eth0. After changing the zone of an interface, you can verify the same using the following command.

The zone change of an interface can affect the status of active servers. For example, If you were working through SSH and moved the zone of the network interface to the one that does not support the SSH service, then your connection might drop, and you cannot log in to the server.
Change the Default FirewallD Zone
If you want to change the default zone, then you can use the –set-default-zone flag to specify the default zone type in the following command.
For example:

After changing the default zone, you can verify the same by running the following command.

Disable FirewallD on CentOS 7
You can disable firewalld permanently or temporarily. If you want to stop or disable the firewalld temporarily, then you can run the following command.

The above command disables the firewalld service until reboot. You can check the status of the firewalld using the below command. The output of this command should appear as “Active: inactive (dead)”, after disabling the firewalld.

If you want to disable the firewalld service permanently, then you need to follow the below steps:
1) First, you need to stop the firewall service by running the following command.

2) After stopping the service, you need to check the status. The output of the status command should state that the service is inactive.

3) Then, you need to disable the service from activating upon system reboot using the following command.
4) Now you have disabled firewalld, but there is a chance that other active services can activate firewalld. To prevent the other services from activating firewalld, you can run the following command. This command masks the firewalld from other services.

So this is how you set up and Install FirewallD on CentOS 7. If you need any further help, please contact our support department.

